- Data Security or Data Breach? How Virtual Data Rooms Protect You
- What is Data Security?
- Why is Data Security crucial?
- What are the varied Types of Data Security Threats?
- What are Some Common Data Security Vulnerabilities?
- What is a Data Breach?
- What is a data breach?
- What are the Consequences of a Data Breach?
- What are some examples of data breaches?
- How can a data breach affect your business?
- What are Virtual Data Rooms?
- What are virtual data rooms?
- How do virtual data rooms work?
- What are the benefits of using a virtual data room?
- How do Virtual Data Rooms Protect Your Data?
- Data Security optimal Practices
- Choosing the Right Virtual Data Room for Your Needs
- How do you select the right virtual data room for your business?
- What are some popular virtual data room offerrs?
- Conclusion

In today’s digital landscape, data is more valuable than ever. Whether you’re a large corporation or a small startup, safeguarding your sensitive information is crucial. But with the ever-present threat of cyberattacks and data breaches, how can you ensure your data remains secure? One powerful tool gaining traction is the Virtual Data Room (VDR). Think of it as a highly secure, online vault, built for storing, managing, and sharing confidential documents with utmost control and transparency.
VDRs are more than just file-sharing platforms. They offer a robust suite of features designed to protect your data from unauthorized access. They use advanced encryption and access controls to ensure only authorized individuals can view and interact with your information. This is where the distinction between data security and data breach becomes incredibly important. With a VDR, you proactively implement data security, significantly minimizing the chances of a costly data breach.
But it’s not just about protection; VDRs are also vital for collaborating and managing complex transactions efficiently. Imagine a real estate deal or merger and acquisition where crucial legal, financial, and operational data needs to be shared and analyzed by multiple parties. VDRs provide a central platform for organized storage and streamlined workflows, minimizing confusion and increasing productivity.
From ensuring due diligence in mergers and acquisitions to safeguarding intellectual property in collaborations, the impact of VDRs extends beyond simply keeping information safe. They enable smooth business processes and help facilitate successful collaborations. This comprehensive approach is why more organizations are recognizing VDRs as a must-have tool in today’s digital world. In the following sections, we’ll dive into the specific benefits of using a VDR and provide you with the essential information to make an informed decision about protecting your data and business.
Data Security or Data Breach? How Virtual Data Rooms Protect You
In today’s digital age, data is arguably the most valuable asset any organization possesses. It fuels business operations, informs strategic decisions, and drives innovation. However, this precious resource is also vulnerable to a multitude of threats, making data security an absolute requirement.
What is Data Security?
Data security refers to the measures taken to protect sensitive information from unauthorized access, use, disclosure, disruption, modification, or destruction. It encompasses a wide scope of practices, technologies, and policies designed to ensure the confidentiality, integrity, and availability of data.
Why is Data Security crucial?
The importance of data security cannot be overstated. Here’s why:
- Protecting Intellectual Property: Data security safeguards valuable intellectual property, including trade secrets, patents, and study findings, which are crucial for a company’s rival benefit.
- Maintaining Customer Trust: A data breach can severely damage customer trust and reputation, leading to financial losses and legal repercussions.
- Ensuring Compliance: Organizations are subject to various data protection regulations, such as GDPR and CCPA, which impose strict requirements for data security.
- Preventing Financial Losses: Data breaches can outcome in financial losses due to theft of sensitive financial information, extortion attempts, and legal expenses.
- Maintaining Operational Efficiency: Data security ensures the smooth functioning of business operations by protecting critical infrastructure and preventing disruptions caused by cyberattacks.
What are the varied Types of Data Security Threats?
The threats to data security are ever-evolving, but some common types include:
- Malware: Viruses, worms, and ransomware can infiltrate systems, steal data, or disrupt operations.
- Phishing: Malicious emails or websites disguised as legitimate sources can trick users into revealing sensitive information.
- Social Engineering: Manipulating individuals to gain access to sensitive information through psychological approachs.
- Denial of Service (DoS) Attacks: Overwhelming a system with traffic to make it unavailable to legitimate users.
- Insider Threats: Employees with access to sensitive data may misuse it for personal gain or unintentionally compromise security.
What are Some Common Data Security Vulnerabilities?
- Weak Passwords: Easily guessed passwords can be easily compromised.
- Unpatched Software: Outdated software is vulnerable to known security flaws.
- Lack of Encryption: Sensitive data transmitted over the internet or stored on devices should be encrypted.
- Poor Access Control: Granting unnecessary access to data can boost the risk of unauthorized use.
- Unsecured Wi-Fi Networks: Public Wi-Fi networks can be easily intercepted, exposing data to unauthorized access.
What is a Data Breach?
A data breach occurs when sensitive information is accessed or stolen by unauthorized individuals. This can be the outcome of a deliberate attack, accidental disclosure, or a combination of factors.
What is a data breach?
A data breach occurs when unauthorized individuals gain access to sensitive information that is stored or transmitted electronically. This could include customer data, financial records, intellectual property, or other confidential information. Data breaches can occur through various means, including malware attacks, phishing scams, social engineering, and insider threats.
What are the Consequences of a Data Breach?
The consequences of a data breach can be far-reaching and devastating for individuals and organizations alike. These include:
- Financial Losses: Stolen credit card information, identity theft, and fraudulent transactions can outcome in significant financial losses.
- Reputational Damage: Public trust can be eroded, leading to a decline in customer loyalty and brand value.
- Legal Penalties: Data protection regulations impose hefty fines for organizations that fail to protect sensitive information.
- Operational Disruptions: Data breaches can disrupt business operations, causing downtime, lost productivity, and customer dissatisfaction.
- Privacy Violations: Stolen personal information can be used for blackmail, extortion, or other criminal activities.
What are some examples of data breaches?
- Equifax Data Breach (2017): Over 147 million individuals’ personal information, including Social Security numbers, was exposed.
- Yahoo Data Breach (2013): Over 3 billion user accounts were compromised in one of the largest data breaches in history.
- Target Data Breach (2013): Millions of credit card numbers and personal information were stolen during the holiday shopping season.
How can a data breach affect your business?
- Loss of customer trust: A data breach can damage your reputation and make customers wary of doing business with you.
- Financial penalties: You could face fines and legal action from regulators and customers.
- Operational disruption: A data breach can disrupt your operations, forcing you to shut down systems and restore data.
- boostd insurance costs: Your insurance premiums could rise as a outcome of a data breach.
What are Virtual Data Rooms?
Virtual data rooms (VDRs) are secure online platforms designed for sharing and managing sensitive information. They offer a controlled environment for storing, accessing, and collaborating on confidential documents.
What are virtual data rooms?
Virtual data rooms (VDRs) are secure online platforms designed to securely store, manage, and share sensitive information. They offer a controlled environment for managing confidential documents during various business processes, such as mergers and acquisitions (M&A), due diligence, fundraising, litigation, and intellectual property management.
How do virtual data rooms work?
VDRs work by providing a secure, cloud-based platform where users can upload, store, and share sensitive information. Users can set access controls to determine who can view, edit, or download specific documents. This ensures that only authorized individuals have access to sensitive information.
What are the benefits of using a virtual data room?
- Enhanced Security: VDRs employ advanced security measures, such as encryption, access control, and audit trails, to protect data from unauthorized access.
- Improved Collaboration: VDRs facilitate seamless collaboration among multiple stakeholders, allowing them to share and access information securely.
- Streamlined Processes: VDRs automate document management and workflow, reducing manual tasks and streamlining business processes.
- Centralized Data Repository: VDRs offer a central repository for all sensitive documents, making them readily available to authorized users.
- boostd Efficiency: VDRs eliminate the need for physical document sharing, saving time and resources.
How do Virtual Data Rooms Protect Your Data?
VDRs employ various security measures to safeguard sensitive information:
- Data Encryption: All data stored and transmitted within a VDR is encrypted using robust algorithms, making it unreadable to unauthorized individuals.
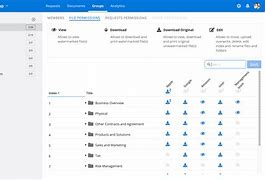
- Access Control and Permissions: VDRs allow administrators to control user access to specific documents and folders, ensuring that only authorized individuals can view or edit sensitive information.
- Auditing and Logging: VDRs keep detailed logs of all user activity, providing an audit trail that can be used to track access patterns and determine potential security breaches.
- Watermarking and Redaction: VDRs allow for the watermarking of documents to determine unauthorized distribution, and they offer redaction capabilities to conceal sensitive information before sharing.
- Two-Factor Authentication: VDRs often require two-factor authentication, where users must offer an additional code or verification step besides their password, adding an extra layer of security.
Data Security optimal Practices
Beyond implementing VDRs, organizations should adopt a thorough approach to data security, including:
- Use strong passwords: Create complex passwords that are difficult to guess and avoid using the same password across multiple accounts.
- Enable two-factor authentication: Enable two-factor authentication for all accounts that store sensitive information.
- Keep your software up to date: Regularly update software to patch security vulnerabilities.
- Be aware of phishing scams: Be cautious of suspicious emails or websites that ask for personal information.
- Train your employees on data security optimal practices: Educate employees about data security threats and optimal practices for protecting sensitive information.
Choosing the Right Virtual Data Room for Your Needs
When selecting a VDR, consider the following factors:
- attributes: select a VDR that offers the attributes you need, such as document management, collaboration tools, and access control.
- Security: Ensure the VDR offerr has robust security measures in place, including data encryption, access control, and audit trails.
- Pricing: Compare pricing models and select a VDR that fits your budget.
- Customer Support: select a offerr that offers reliable customer support and technical assistance.
How do you select the right virtual data room for your business?
When choosing a VDR, several factors come into play:
- Industry-specific attributes: Some VDRs offer attributes tailored to specific industries, such as healthcare or finance, which can be crucial for meeting regulatory compliance requirements.
- Scalability: Ensure the VDR can accommodate your current needs and can scale with your business growth.
- Integration capabilities: Consider whether the VDR integrates with your existing systems, such as your CRM or accounting software.
- User experience: select a VDR with an intuitive interface that is easy to use for all stakeholders.
What are some popular virtual data room offerrs?
Some popular VDR offerrs include:
- Diligent: Known for its thorough attributes and security, Diligent is a leading offerr of VDRs.
- Intralinks: Intralinks offers a robust platform with advanced security measures, including two-factor authentication and encryption.
- Firmex: Firmex offers a user-friendly interface and a wide scope of attributes, including document management, collaboration tools, and access control.
Conclusion
Data security is paramount in today’s digital landscape. Virtual data rooms play a crucial function in protecting sensitive information, providing a secure platform for sharing, managing, and collaborating on confidential documents. By implementing VDRs and adopting optimal practices for data security, organizations can mitigate risks, protect their valuable assets, and build trust with stakeholders.
Summary of the benefits of using virtual data rooms for data security:
- Enhanced Security: VDRs employ advanced security measures, such as encryption, access control, and audit trails, to protect data from unauthorized access.
- Improved Collaboration: VDRs facilitate seamless collaboration among multiple stakeholders, allowing them to share and access information securely.
- Streamlined Processes: VDRs automate document management and workflow, reducing manual tasks and streamlining business processes.
- Centralized Data Repository: VDRs offer a central repository for all sensitive documents, making them readily available to authorized users.
- boostd Efficiency: VDRs eliminate the need for physical document sharing, saving time and resources.
Call to action:
As you navigate the complexities of the digital world, embrace virtual data rooms as a powerful tool for data security. Learn more about VDRs and implement them in your business to safeguard your valuable data and build a foundation of trust and security.