- How to Safely Share Sensitive Documents with Virtual Data Rooms
- What are Virtual Data Rooms?
- The History of VDRs and Their Evolution
- How Do VDRs Work?
- Why Are VDRs crucial?
- Why Use a Virtual Data Room for Sensitive Document Sharing?
- Choosing the Right Virtual Data Room offerr
- Setting Up Your Virtual Data Room
- optimal Practices for Secure Document Sharing in Virtual Data Rooms
- Common Uses for Virtual Data Rooms
- Security attributes of Virtual Data Rooms
- Tips for selecting the Right Virtual Data Room offerr
- Conclusion

How to Safely Share Sensitive Documents with Virtual Data Rooms
In today’s digital world, businesses are constantly dealing with sensitive information that needs to be shared securely. Whether it’s financial data, intellectual property, or confidential client information, safeguarding this data is paramount. Virtual data rooms (VDRs) have emerged as a powerful solution for securely sharing sensitive documents, offering a robust and efficient way to manage and control access to critical information.
What are Virtual Data Rooms?
Virtual data rooms (VDRs) are secure online platforms designed to facilitate the sharing and management of sensitive documents. They offer a centralized repository for storing, organizing, and controlling access to critical data, making them ideal for various business processes, including mergers and acquisitions (M&A), due diligence, legal discovery, and more.
The History of VDRs and Their Evolution
The idea of virtual data rooms originated in the 1990s, primarily used in large M&A transactions. Initially, VDRs were often physical data rooms, requiring companies to transport and store physical documents in secure locations. With the advent of the internet and cloud computing, virtual data rooms evolved, becoming more accessible and user-friendly. Today, VDRs are widely adopted across various industries, offering a thorough suite of attributes for secure document sharing and management.
How Do VDRs Work?
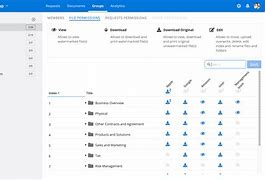
VDRs work by providing a secure online environment where users can upload, organize, and share documents. Users are granted specific access permissions, allowing them to view, download, or edit documents based on their functions and responsibilities.
Key attributes that enable secure document sharing in VDRs include:
- Data encryption: VDRs encrypt data at rest and in transit, ensuring that sensitive information remains protected throughout its lifecycle.
- Access controls: VDRs allow administrators to set granular access permissions, controlling who can view, download, or edit specific documents.
- Watermarking and document tracking: VDRs can watermark documents and track their access history, providing a clear audit trail of who viewed and downloaded what.
- Audit logs and activity monitoring: VDRs maintain detailed audit logs of all user activity, providing a thorough record of data access and modifications.
Why Are VDRs crucial?
VDRs are essential for businesses that handle sensitive information due to their ability to offer:
- Data security and compliance: VDRs comply with industry regulations like GDPR and HIPAA, ensuring that sensitive information is protected and managed in accordance with legal requirements.
- Protection of intellectual property: VDRs help businesses safeguard their intellectual property, preventing unauthorized access and ensuring confidentiality.
- Streamlining due diligence processes: VDRs simplify due diligence processes by providing a secure platform for sharing and reviewing critical documents.
- Facilitating mergers and acquisitions (M&A) activities: VDRs streamline M&A transactions by providing a secure and efficient platform for sharing and managing sensitive information.
- Enhancing collaboration and communication: VDRs facilitate seamless collaboration by providing a shared workspace where teams can access and contribute to documents.
Why Use a Virtual Data Room for Sensitive Document Sharing?
In addition to the benefits mentioned above, using VDRs for sensitive document sharing offers several benefits:
- Enhanced security: VDRs offer robust security measures that traditional methods lack, ensuring that sensitive data remains protected from unauthorized access.
- Improved efficiency: VDRs simplify document sharing and management, saving time and resources compared to manual processes.
- boostd control: VDRs empower businesses to control access to sensitive data, ensuring that only authorized individuals can view or modify it.
- Enhanced compliance: VDRs help businesses meet regulatory requirements by providing secure and auditable platforms for handling sensitive data.
Choosing the Right Virtual Data Room offerr
selecting the right VDR offerr is crucial for ensuring secure and efficient document sharing. Consider these factors when making your decision:
- attributes and functionalities: Look for VDR offerrs that offer a thorough set of attributes, including secure file sharing, user management, access control, and audit logging.
- Security measures and certifications: select offerrs with robust security measures, such as data encryption, two-factor authentication, and compliance with industry standards like SOC 2 and ISO 27001.
- Pricing and paid access models: Evaluate varied pricing plans and paid access models to find a offerr that fits your budget and needs.
- Customer support and technical assistance: Ensure that the offerr offers responsive and reliable customer support to address any technical issues or querys.
- Industry-specific solutions: Some VDR offerrs offer specialized solutions tailored to specific industries, such as healthcare, finance, or legal.
Setting Up Your Virtual Data Room
Once you’ve chosen a VDR offerr, setting up your data room is a straightforward process:
- Creating your VDR account: Register for a VDR account and offer the necessary information, including your business details and contact information.
- Uploading and organizing documents: Upload your documents to the VDR platform and organize them into folders or subfolders for easy navigation.
- Setting access permissions and user functions: Define specific access permissions for each user, granting them appropriate levels of access to documents based on their functions and responsibilities.
- Implementing security protocols: Configure security protocols, such as two-factor authentication, password complexity requirements, and data encryption.
- Ensuring data integrity and version control: Implement data integrity checks and version control to maintain the accuracy and reliability of documents.
optimal Practices for Secure Document Sharing in Virtual Data Rooms
To ensure the highest level of security when sharing sensitive documents in a VDR, follow these optimal practices:
- Only share documents with authorized users: Ensure that only individuals with legitimate access to the information are granted permission to view or download documents.
- Utilize strong passwords and two-factor authentication: Encourage users to create strong passwords and enable two-factor authentication for added security.
- Implement data encryption and access controls: Ensure that all data is encrypted both at rest and in transit, and set granular access controls to restrict access to specific individuals or groups.
- Regularly monitor and audit VDR activity: Monitor user activity logs regularly to determine any suspicious behavior or unauthorized access attempts.
- Educate users on security optimal practices: offer training to users on security optimal practices for handling sensitive data, including password security, data handling, and reporting suspicious activity.
Common Uses for Virtual Data Rooms
VDRs have become essential tools for various business processes, including:
- Due diligence in mergers and acquisitions: VDRs streamline due diligence processes by providing a secure platform for sharing and reviewing financial statements, contracts, and other sensitive documents.
- Financial reporting and audits: VDRs facilitate secure sharing of financial reports and supporting documentation with auditors, ensuring compliance and transparency.
- IP licensing and asset management: VDRs offer a secure environment for managing and sharing intellectual property documents, licensing agreements, and other critical information.
- Legal discovery and e-discovery: VDRs assist in legal discovery by providing a centralized repository for storing and sharing evidence, facilitating efficient and secure document review.
- Real estate transactions: VDRs simplify real estate transactions by enabling the secure sharing of property documents, contracts, and other pertinent information.
- Government and public sector projects: VDRs are used in government and public sector projects to ensure secure collaboration and data sharing, maintaining transparency and accountability.
Security attributes of Virtual Data Rooms
VDRs offer thorough security attributes to protect sensitive data:
- Encryption at rest and in transit: VDRs encrypt data at rest, ensuring that information remains secure even if the underlying storage system is compromised. Data is also encrypted in transit, protecting it during transmission.
- Access controls and user authentication: VDRs implement robust access controls, allowing administrators to define specific access levels for varied users. Two-factor authentication adds an extra layer of security, requiring users to offer two forms of identification before accessing the VDR.
- Watermarking and document tracking: VDRs can watermark documents with unique identifiers, making it easy to track their distribution and determine any unauthorized copies. Document tracking logs offer detailed records of document access history.
- Audit logs and activity monitoring: VDRs maintain detailed audit logs of all user activity, including login attempts, document downloads, and changes made to documents. This information helps determine suspicious activity and ensure data integrity.
- Compliance with industry regulations: VDRs are designed to comply with industry regulations like GDPR, HIPAA, and SOC 2, ensuring that sensitive data is handled in accordance with legal requirements.
Tips for selecting the Right Virtual Data Room offerr
Choosing the right VDR offerr is a crucial step in securing your sensitive information. Consider these factors:
- Consider your specific security requirements: Evaluate your security needs based on the sensitivity of the data you will be sharing and the regulations you must comply with. select a offerr that offers robust security attributes that align with your requirements.
- Compare attributes, pricing, and customer support: study varied VDR offerrs and compare their attributes, pricing plans, and customer support services. Look for offerrs that offer a balance of functionality, affordability, and responsive support.
- Look for certifications and industry recognition: select offerrs that have obtained pertinent industry certifications, such as SOC 2 or ISO 27001, demonstrating their commitment to security and compliance.
- Request a demo and trial access: Request a demo of the VDR platform and a trial access period to test its attributes and usability before making a final decision.
Conclusion
Virtual data rooms are indispensable tools for businesses that handle sensitive information, offering a secure and efficient way to share and manage critical data. By implementing robust security attributes, controlling access permissions, and adhering to optimal practices, businesses can leverage VDRs to protect their intellectual property, streamline due diligence processes, and ensure compliance with industry regulations.
Remember to select a reputable VDR offerr that meets your specific needs and consider obtaining expert guidance to ensure that your data room is properly set up and maintained. By taking the necessary steps to secure your sensitive information, you can protect your business and build trust with your stakeholders.